There is a lot of rogue websites out there. These are sites set up for no other purposes than to steal personal information and money, or to spread malware. Well-made rogue websites are often distinguishable from genuine ones and you need to look closely at their mode of operation to understand that they are fraudulent. For network users, it is important to avoid visiting rogue sites. There now exist tools that is supposed to help with this. However, some of these tools appear to be broken.
Recently, a reader informed me that one of the web-pages on the site you are reading now (my personal website) was flagged by Norton Internet Security Online as a phishing site.
Phishing is a term used in the field of computer security to describe the act of tricking someone into giving away confidential information by masquerading as a trustworthy person or business. One common form of phishing is to impersonate a legitimate website with the intent to coerce users to give away information.
The URL flagged as dangerous was http://hannemyr.com/photo/flash.html#nettl, and Norton attached the verdict “known phishing site“ (kjent nettfiskingsside) to it. [The page has changed since 2007, but the link goes to the version of it Norton flagged as dangerous.] A part of the security warning page that Norton pops up if you try to visit my site (in Norwegian) is shown below. Click on the image to see a full screen dump.
The webpage in question is a simple text page and read-only. It doesn't ask the user for any type of information. Why Norton Internet Security Online arrived at the conclusion this page is part of a phishing site is a mystery.
Verified?
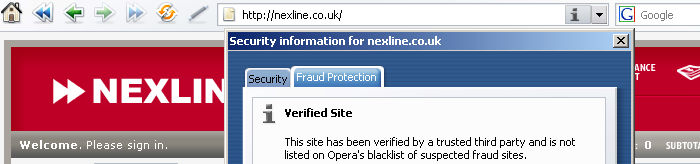
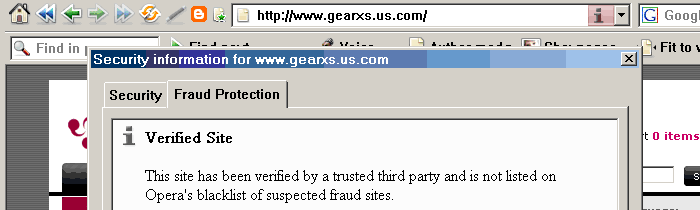
False positives are bad, but giving crooks a “verified“ seal of approval is worse. Below are two screen dumps of the verification tool built into the Opera web browser concerning the websites nexline.co.uk and gearxs.us.com. Each is reported as a “Verified Site“ that “has been verified by a trusted third party“.
These two sites does not impersonate other sites, but they masquerade as legitimate e-commerce sites, which they are not. For the record, both were at the time the above screen shots were recorded (fall 2006) well known fraud sites set up for phishing and for receiving advance payment without ever delivering merchandise. They've since been taken down.
There is a description of the MO of gearxs.us.com at aa419.org. Briefly, it featured a bogus BBB Reliability Seal (hint: the seal's URL is not at BBB), and its checkout page was un-secure, and tried to trick marks into typing in their credit card number, expiry date, CVV2 code, and social security number (SSN) in order to buy electronics good at prices to good to be true. No legitimate merchant needs to know his customer's SSN, but an identity thief does.
My confidence in tools did not improve when I turned to anti-phishing site PhishTank to check their verdict, only to find that they also had failed to identify the site correctly as a phishing site.
Another site reporting on the “safeness” of websites is name ScamAdviser.com. In June 2012, it gave a “High Trust Rating” to GoodleAdz.com, a website that was running an blatantly obvious Ponzi scheme. It also insists the site is “Very popular”, but no source is given.

There is no information on ScamAdviser.com about who is running the site, or how they compute their trust rating. The FAQ only state that:
We are unique in that we are trying to amalgamate many different sources of information and report more detailed information such as where we think the website is really from. It's not a 100% science but our algorithm is changing constantly catch these rascals. There are so many fraud and fake sites popping up and we provide the data to help you identify these.
Closing Note
I don't know why Norton flagged my site as a known phishing site, or why the anti-phishing tool built into Opera gave two well known fraud sites a clean bill of health.
However, I suspect that part of the problem is that many anti-internet-fraud efforts are crowd-sourced, and with very little quality assurance in place.
A case in point is PhishTank.com. It appears to rely entirely on random reviewers only known by their handles to be able to correctly call a fraudulent site based upon no published criteria. From the look of it, the people serving as reviewers at PhishTank are able to spot phishing sites that impersonate well known brand sites with bogus URL. For instance, when a site claiming to be http://paypal.com is located on this weird URL: http://www.paypal.com.t9pn9fhrdzxix7c8ev2.com/cgi-bin/webscr/?login-dispatch=marc@die.de&login-proc=ok, the PhishTank reviewers are able to tell that it is a phishing site. But they haven't a clue about how to identify sites like http://gearxs.us.com as fraudulent, and end up giving the crooks running such sites a clean bill of health.
Acknowledgements
Thanks to Jarle Lund for providing the screen dump from Norton Internet Security Online.